Attack Tree Modeling
Visit attacktree.online for the free SaaS edition, a complete attack tree modeling platform that encompasses security control integration and risk simulation capabilities.

This absolutely free SaaS edition offers a comprehensive feature set for attack tree modeling, with all data managed client-side in the browser for your convenience. This approach ensures no registration is required, maintaining your data privacy with no data stored on servers, no use of cookies, and absolutely no tracking of any kind.
For those seeking enhanced customization and backend integration options, upgrades to the Custom SaaS Edition or the Self-Hosted Edition are possible. However, this upgrade is entirely optional, ensuring that you have the flexibility to choose the solution that best fits your needs.
Tree Creation
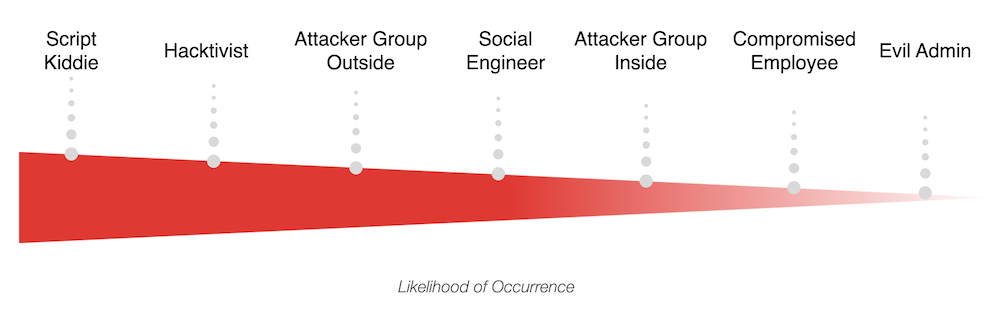
The attack tree modeling process begins with the optional customization of threat actors and their capabilities, allowing you to tailor the model to specific security concerns:
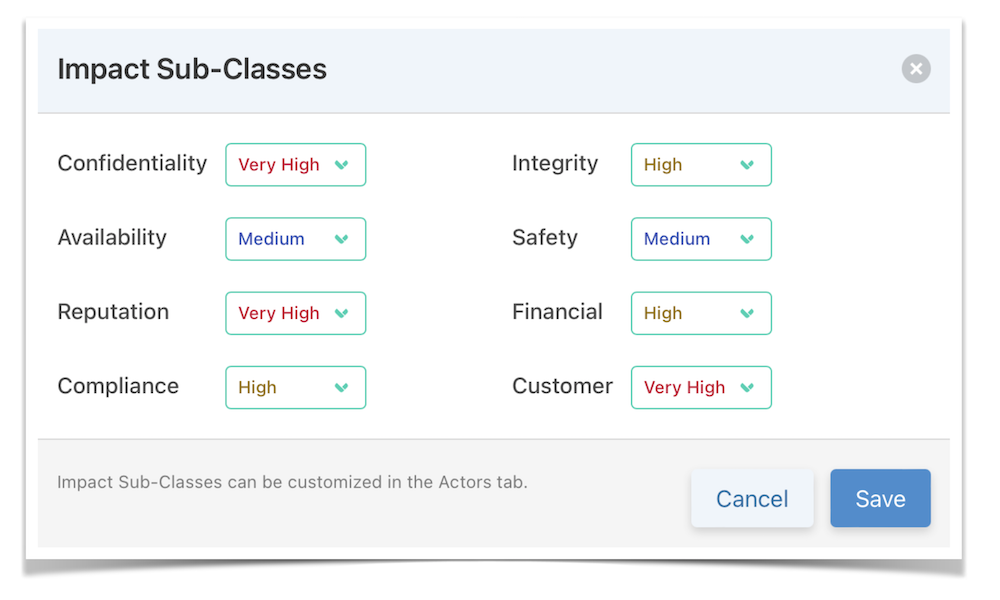
You’ll then model the attack goals, focusing on what the threat actors aim to achieve. For each goal you define the potential impact on your business, customers, and other stakeholders:
Next, the process entails building the tree by outlining the steps necessary to achieve these goals via diverse attack paths. Each leaf node, representing the attack vectors, is assigned specific actors and complexity levels:
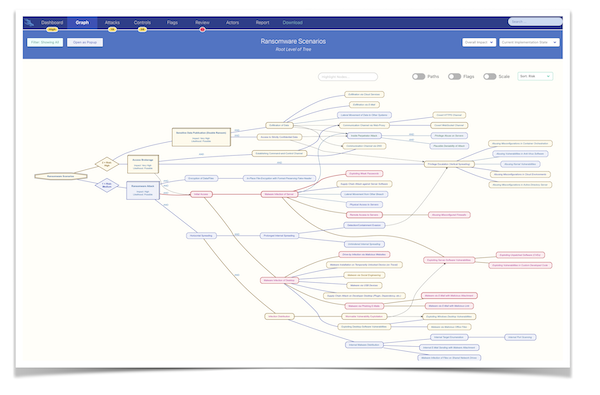
The result is a detailed attack tree model, serving as a foundation for the integration of security controls:
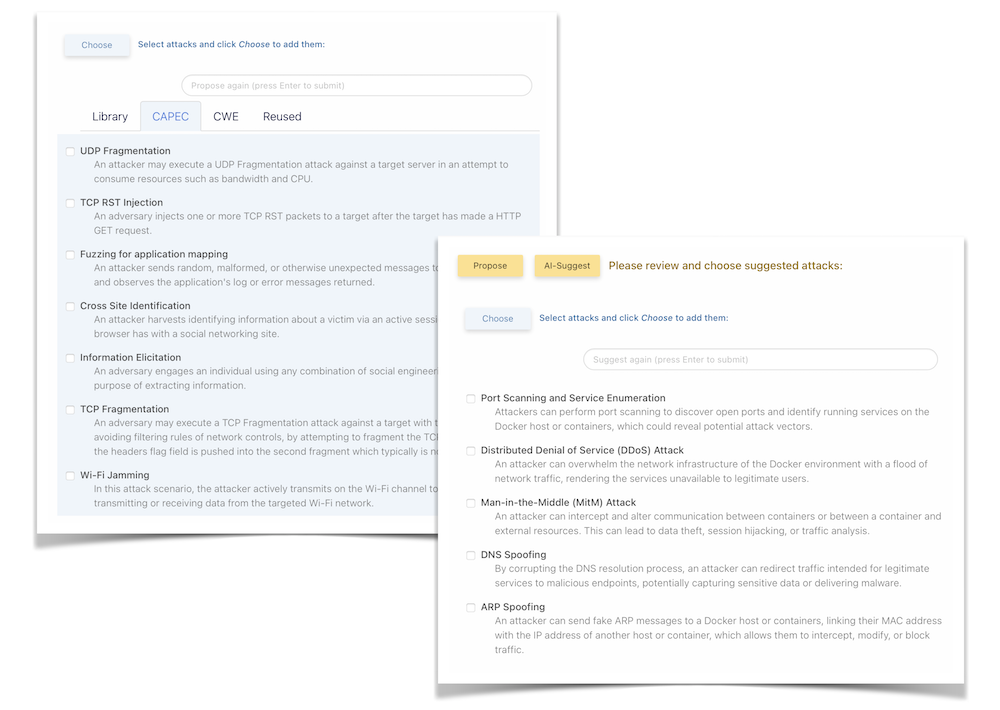
To improve the creativeness of adding attack vectors, the integrated proposals library (with MITRE CAPEC and CWE included) and the optional AI-suggestion feature can be used to provide you with additional ideas:
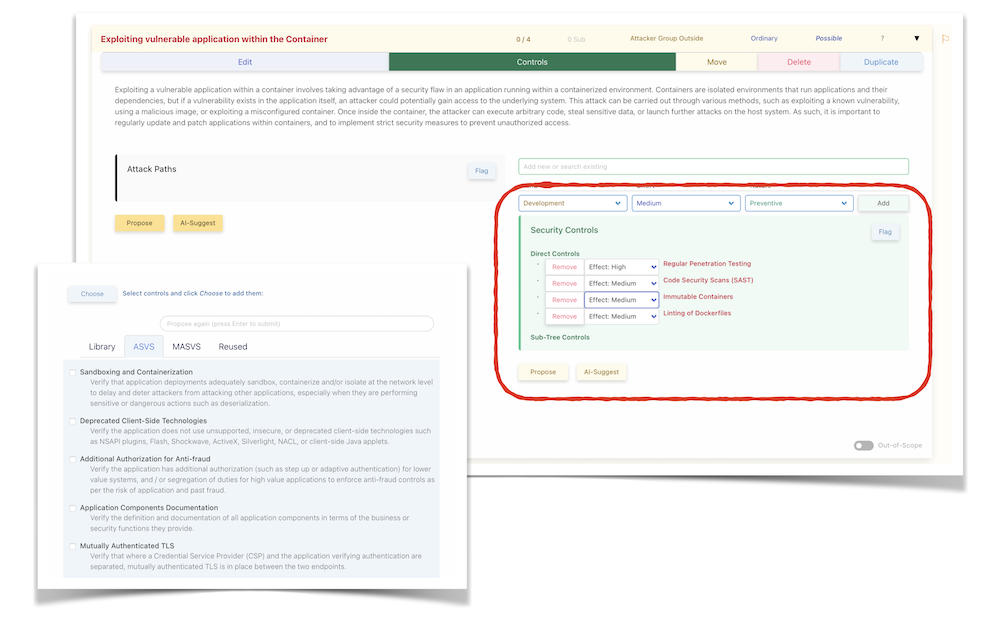
Security Controls
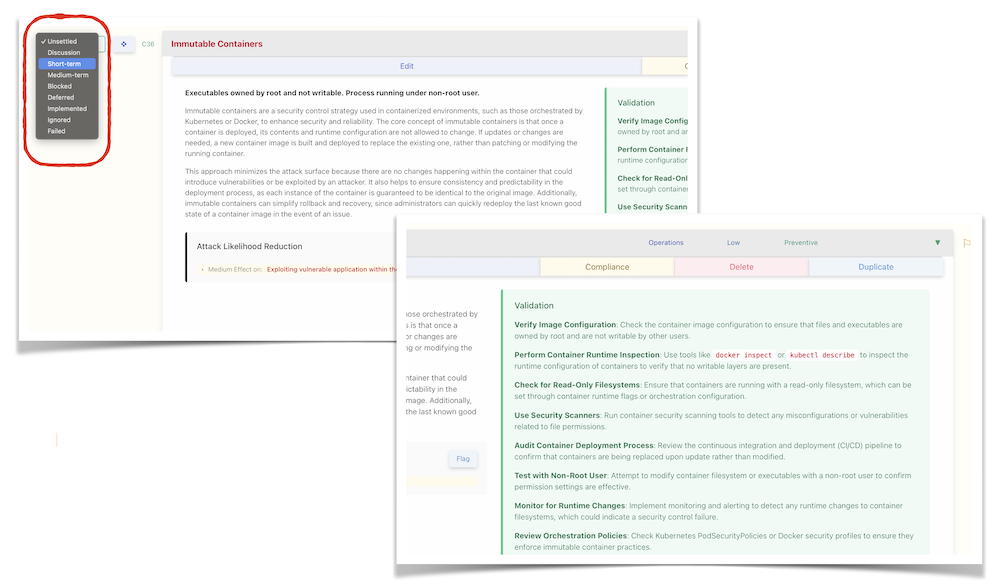
The next phase involves the addition of Security Controls, which can range from preventive and detective to compensatory measures. These controls can be added directly to nodes in the model, or through the use of proposal templates (with OWASP ASVS and MASVS included) and the optional AI-suggestion feature for added efficiency. The positioning of controls is strategic; the closer to the root, the more generic their application, while placement towards the leaves indicates specificity. You can also define the effectiveness and costs of each control, helping you prioritize implementation:
Finally, assigning a status to each control not only provides a clear view of the current risk level but also tracks the progress of implementation. Additionally, utilize the optional validation steps to confirm, during internal audits or similar evaluations, the correct implementation of these controls:
Review & Risk Simulation
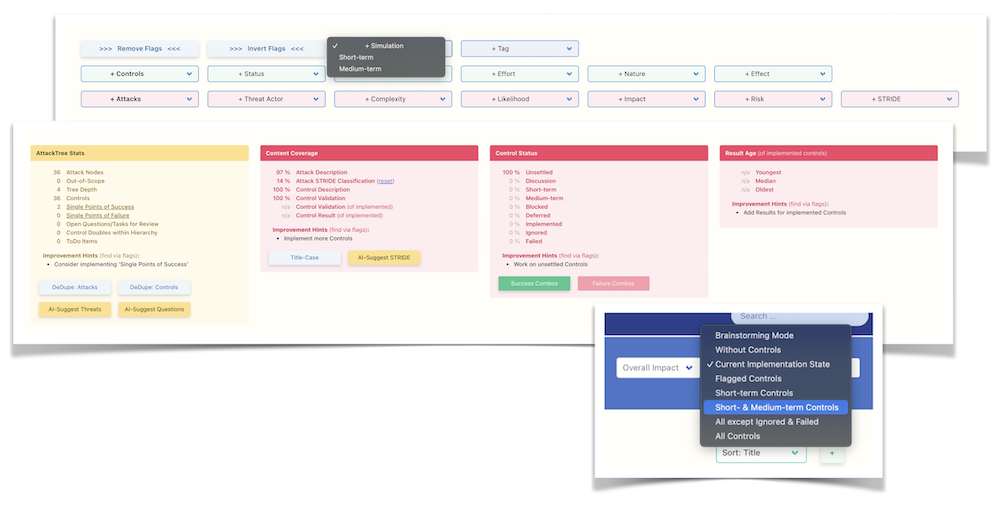
The Risk Simulation module offers a variety of simulation methods to thoroughly analyze potential security threats. Engage in two-step roadmap simulations to conduct what-if analysis, enabling you to envision various security scenarios and their outcomes:
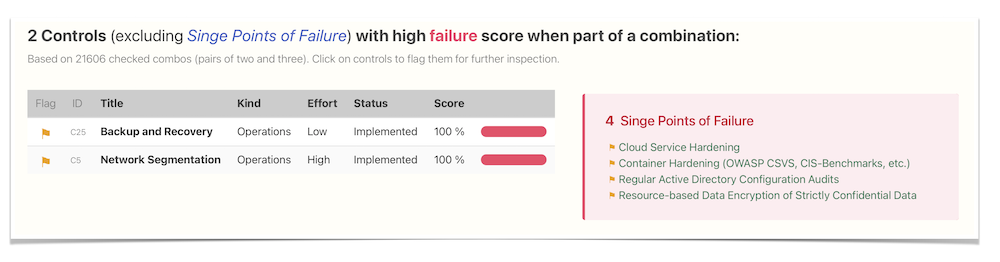
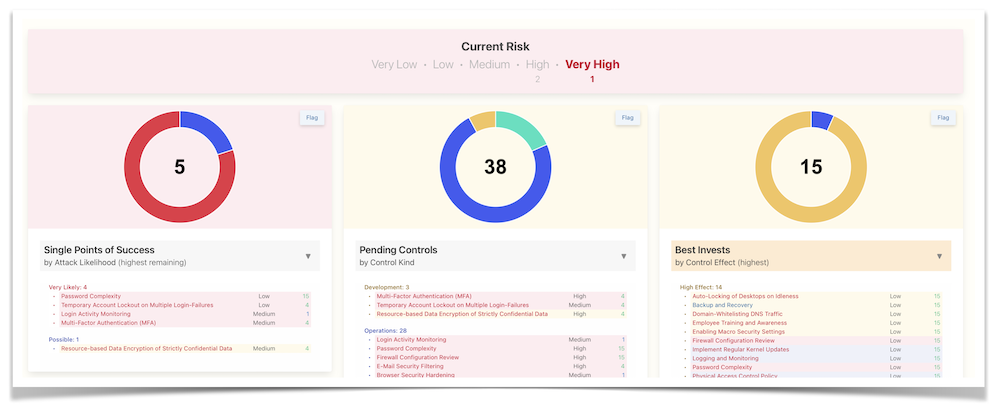
Utilize the Monte Carlo simulation, among other techniques, to pinpoint the most critical attack paths, identify single points of success, and detect any Achilles heels in your system. This comprehensive analysis culminates in the creation of a prioritized roadmap, guiding the strategic implementation of security controls to fortify your defenses effectively:
Reporting & API
Experience the convenience of our interactive dashboard, designed to present all critical information at a glance for quick and efficient analysis:
The system offers comprehensive reporting that encapsulates every detail of the attack tree, security controls, and risk simulation outcomes. For enhanced versatility, you have the option to export the complete attack tree or specific subtrees in SVG format, comprehensive reports as customizable PDFs, and detailed control-attack mappings in Excel format:
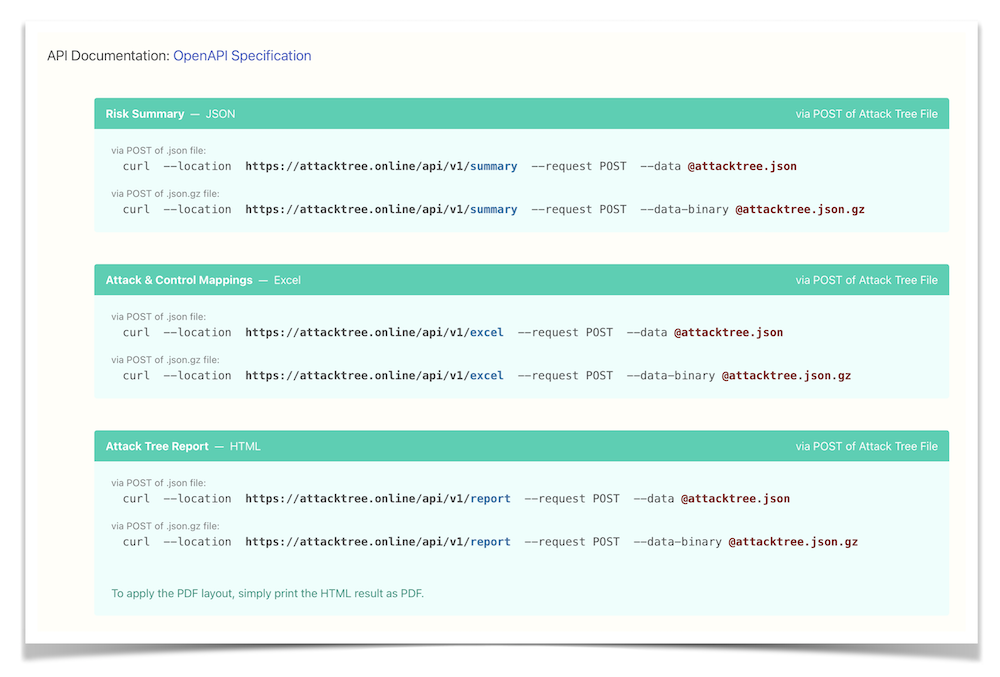
Furthermore, our robust API enables seamless integration of attack tree modeling, security control management, and risk simulation features into your existing toolchain, streamlining your cybersecurity processes.
Deep Customization
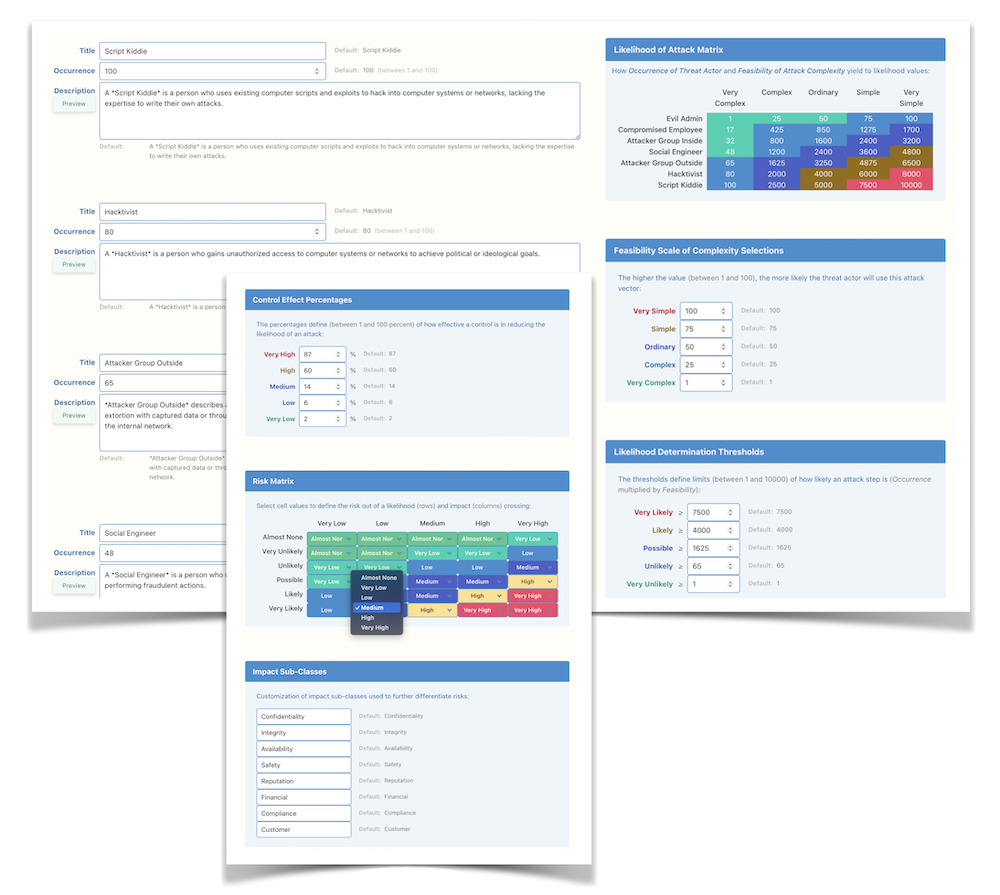
The platform offers extensive customization capabilities. You can modify threat actor capabilities to better match your security landscape and adjust impact subclasses to more accurately represent your risks. Tailoring is available for likelihood thresholds, control effect levels, and the configuration of the risk matrix to meet your specific needs. Furthermore, report customization allows you to focus on the most relevant data, ensuring your cybersecurity reporting is both effective and insightful:
Micro Attack Simulations
The attack tree approach, as showcased at recent conference talks in 2023 at BruCON and DeepSec, enables the implementation of micro attack simulations as part of live assessments. This method allows for the execution of targeted simulations to validate specific implemented security controls. It offers a practical alternative to conducting a full-scale red-team engagement, making it an efficient and focused way to test and strengthen your cybersecurity resilience.
Free SaaS Edition
All of these features and more are available in the Free SaaS Edition at attacktree.online.
For even deeper customization and integration options, check out the Custom SaaS Edition or the Self-Hosted Edition.