Tips for handling the Log4j vulnerability
This blog post tries to summarize the current state of advice regarding the Log4j vulnerability, which is known as Log4Shell and associated with CVE-2021-44228, CVE-2021-45046, CVE-2021-45105, CVE-2021-4104, and CVE-2021-44832.
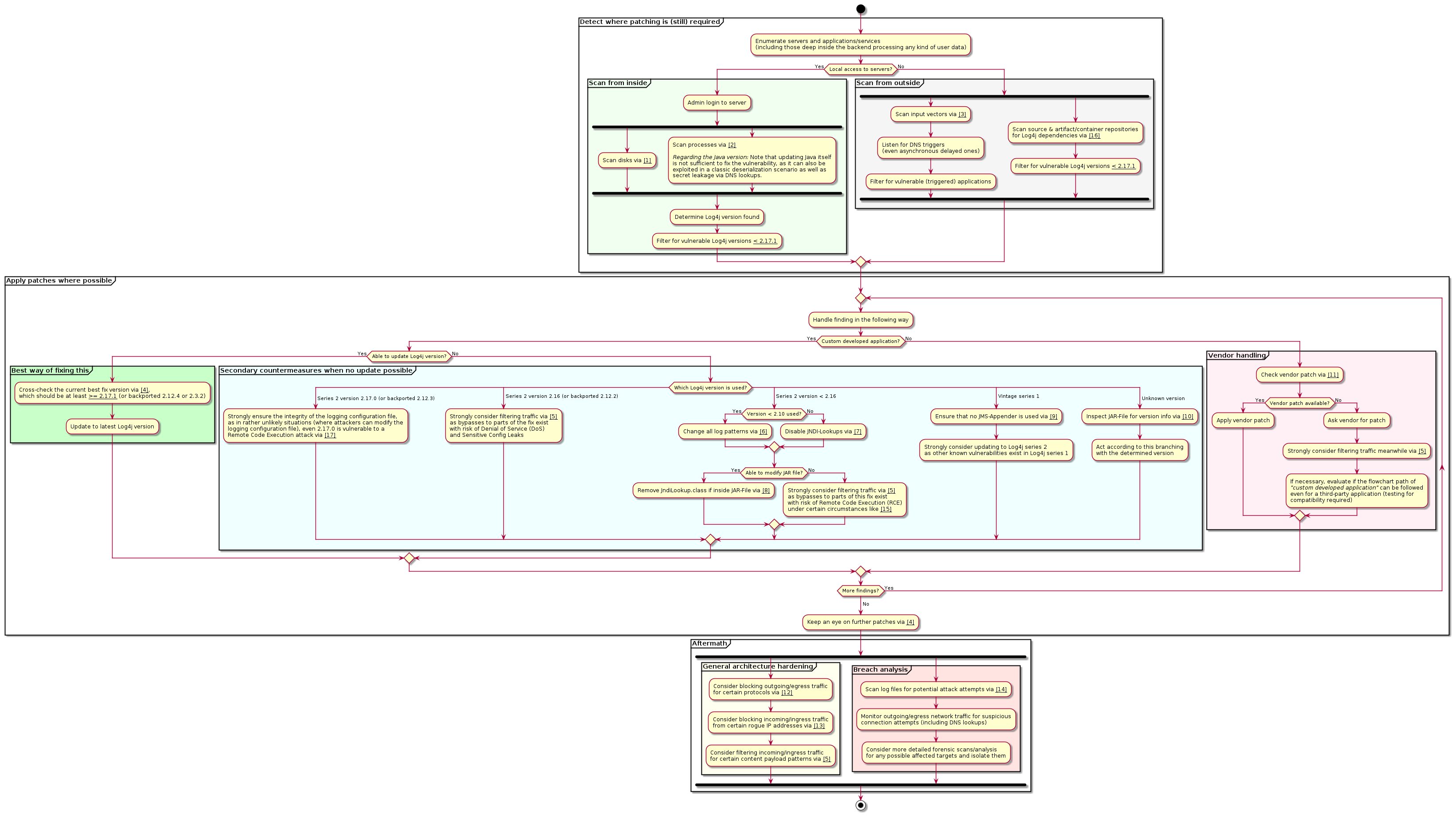
Please check this flowchart of how to proceed in handling this vulnerability (click to enlarge):
References from within the flowchart
Please open the flowchart diagram first and then follow the relevant references from there (by number in chart).
[1] Scanning disks for Log4j
https://github.com/mergebase/log4j-detector
https://github.com/fox-it/log4j-finder
https://github.com/hillu/local-log4j-vuln-scanner
https://github.com/jfrog/log4j-tools
https://github.com/CERTCC/CVE-2021-44228_scanner
https://github.com/aquasecurity/trivy
[2] Scanning running processes for Log4j
Remember to adjust the script ideas as needed, like for example the path…
Some script idea: ps -ef | grep [j]ava | while read user pid rest ; do echo $user $pid $rest ; lsof -np $pid | grep -i log4j ; done
Some script idea: lsof -np $(pgrep -d, -f java) 2>&1 | grep -i log4j
Some script idea: lsof | grep -i log4j
Some script idea: ps aux | egrep '[l]og4j'
Some script idea: find / -iname "log4j*"
Some script idea: find / -name '*[wj]ar' -print -exec sh -c 'jar tvf {} | grep -i log4j' \;
YARA rule to detect the presence of Log4j in memory: https://github.com/bi-zone/Log4j_Detector
[3] Scanning input vectors (like parameters) of applications and services
https://github.com/fullhunt/log4j-scan
https://github.com/silentsignal/burp-log4shell
https://github.com/projectdiscovery/nuclei-templates/blob/master/cves/2021/CVE-2021-44228.yaml
https://github.com/huntresslabs/log4shell-tester
[4] Apache Log4j security patches
Remember to cross-check the latest version, as also 2.17.0 was vulnerable to a Remote Code Execution (under certain circumstances where an attacker can modify the logging config file): https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44832
https://logging.apache.org/log4j/2.x/security.html
[5] Filtering for certain malicious patterns
https://github.com/back2root/log4shell-rex
https://github.com/Neo23x0/log4shell-detector
https://github.com/woodpecker-appstore/log4j-payload-generator
https://coreruleset.org/20211213/crs-and-log4j-log4shell-cve-2021-44228/
[6] Change log patterns
Change from %m to %m{nolookups}
[7] Disable JNDI lookups
Add ‐Dlog4j2.formatMsgNoLookups=true to JVM start or export LOG4J_FORMAT_MSG_NO_LOOKUPS=true as environment variable
[8] Remove JndiLookup.class from Log4j JAR file
Remove from single JAR file: zip -q -d log4j-core-*.jar org/apache/logging/log4j/core/lookup/JndiLookup.class
Remove disk-wide from all JAR files: find ./ -type f -name "log4j-core-*.jar" -exec zip -q -d "{}" org/apache/logging/log4j/core/lookup/JndiLookup.class \;
Remember to keep backups of modified files and ensure that the applications’ logging does not rely on the removed feature (JNDI Lookups), which would then be broken.
[9] Apache Log4j vintage series 1 is vulnerable under certain conditions
https://nvd.nist.gov/vuln/detail/CVE-2021-4104
https://github.com/apache/logging-log4j2/pull/608#issuecomment-990494126
[10] Inspect Log4j JAR file for version info
https://github.com/mergebase/log4j-detector
[11] Vendor statements regarding the Log4j vulnerability
https://github.com/cisagov/log4j-affected-db
https://github.com/YfryTchsGD/Log4jAttackSurface
https://github.com/NCSC-NL/log4shell/blob/main/software/README.md
[12] Blocking outgoing/egress internet traffic
Try to block or whitelist outgoing internet traffic (especially for protocols LDAP, LDAPS, RMI, IIOP, HTTP, HTTPS and also for ports 389, 12344, 1389, 5557, 5875)
[13] Blocking incoming/ingress traffic from rogue IPs
https://gist.github.com/blotus/f87ed46718bfdc634c9081110d243166
[14] Scan log files and check for attack attempts
https://gist.github.com/Neo23x0/e4c8b03ff8cdf1fa63b7d15db6e3860b
https://github.com/Neo23x0/log4shell-detector
Some short strings (can cause false positives) to scan for case-insensitive: ${${ or ${::- or %24%7B%3A%3A- or ${env: or ${date: or ${lower: or ${upper: or ${main: or ${sys: or ${ctx: or ${java: or /a} or hostName} or }${ or ${
Scanning for Indicators of Compromise (IoC): https://github.com/NCSC-NL/log4shell/blob/main/iocs/README.md
Remember to always check for latest updates of these and other tools/scanners.
[15] Some bypass examples of the fix in 2.15.0 leading to RCE
https://twitter.com/marcioalm/status/1471740771581652995
https://twitter.com/pwntester/status/1471465662975561734
[16] Scanning container images, repos, and dependency tree for Log4j
https://github.com/aquasecurity/trivymvn dependency:tree | grep log4j
Also consider putting known vulnerable Log4j versions on your Maven or Gradle exclusion lists to avoid accidental usage via transitive dependencies.
[17] Remote Code Execution vulnerability in 2.17.0 with limited exploitability leading to RCE
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-44832
https://logging.apache.org/log4j/2.x/security.html