Mitigating Risks the Agile Way
Prior to conducting the training with your team, we’ll have an initial scoping meeting. This session is designed to customize the workshop to your specific requirements, helping us decide on the most suitable approach and focus areas to address your needs effectively.
Top-Down — Attack Scenario Approach
This approach is best suited for teams that are new to threat modeling and want to get started quickly, even in situations where not many details about the architecture are known. This approach is also best suited for teams that want to focus on the most important risks first, based on the most likely attack scenarios.
Bottom-Up — Dataflow Approach
This approach is best suited for teams that already have some experience with threat modeling and want to get a detailed view of the architecture, including all dataflows and their security properties. Focus is more on the architecture itself and less on the most likely attack scenarios. For this approach, usually more details about the architecture are required upfront.
Initial Model Creation
In the initial segment of the workshop, my focus will be on gaining a comprehensive understanding of your architecture and key security elements. To achieve this, I’ll employ a methodical approach, leveraging my extensive background in development, penetration testing, and threat modeling.
This involves an in-depth inquiry, where I’ll ask a series of targeted questions designed to assess various aspects, including:
- Vulnerabilities in software architecture
- Vulnerabilities in critical business functions, like payment etc.
- Vulnerabilities in authentication & authorization (including tenant isolation)
- Vulnerabilities in exposed and consumed communication interfaces
- Vulnerabilities in consumed data formats
- Vulnerabilities in containerization and their orchestration
- Vulnerabilities in cloud connections
- Vulnerabilities in authentication and authorization
- Vulnerabilities in encryption and digital trust handling
- Vulnerabilities in transfer and storage of sensitive data
- Vulnerabilities in definition of trust boundaries
Following the initial phase, I will enter the rework stage where I’ll develop a preliminary version of the threat model, achieving approximately 70% completion. This model will be crafted based on the responses and insights gathered earlier.
Depending on our agreed-upon strategy, the model will either adopt a top-down, attack scenario-based framework, or a bottom-up, dataflow-based approach. Importantly, I’ll use free tools for this creation, ensuring you have the ability to independently continue refining and working with the threat model.
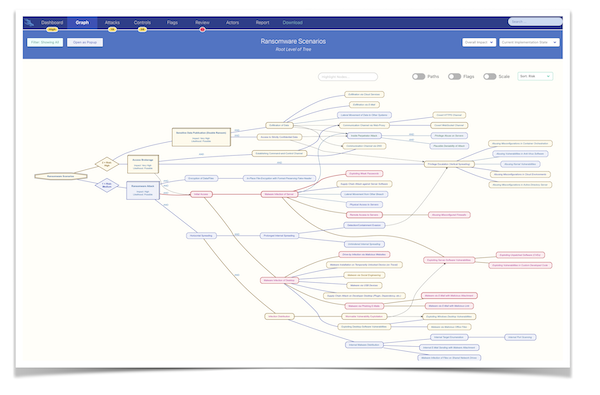
Scenario-Based Models with AttackTree
The top-down approach is best visualized with my free AttackTree toolkit, which allows for a very intuitive way of creating attack trees with security controls to simulate attack scenarios.
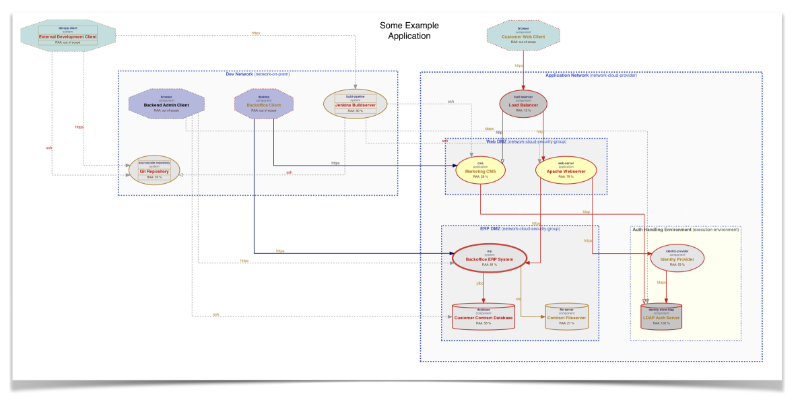
Dataflow-Based Models with Threagile
The bottom-up approach is best visualized with my free Threagile toolkit, where all components, dataflows, and their properties are modeled in a YAML file. This allows for a very detailed view of the architecture elements, including their security properties.
Model Refinement & Simulation
Following my rework phase, I will present the initial threat model to your team in our next workshop session. Here, we’ll collaboratively refine the model, focusing on enriching details, eliminating inaccuracies, and incorporating additional risks that weren’t initially identified.
This interactive process offers the team valuable insights into threat modeling and risk identification, bypassing the complexities often encountered when developing a model from the ground up. As the remaining 30% of the model’s creation typically unfolds in this session, it provides a comprehensive understanding of the entire process.
Detailed Reporting
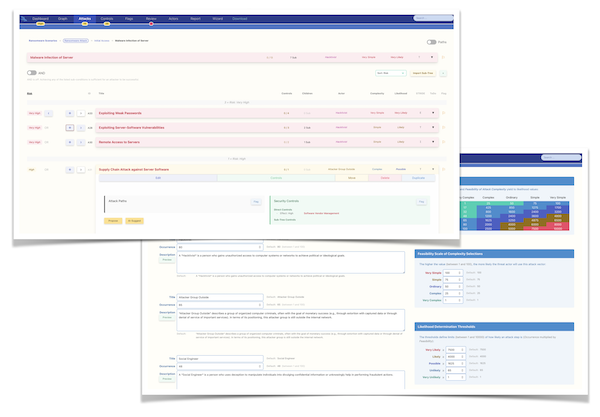
At the conclusion of our workshop, you will receive a comprehensive report detailing the identified risks, complete with thorough descriptions, collected evidence, and tailored mitigation strategies. This report aims not only to address each issue but also provides security controls and recommendations for enhancing your application’s security. To streamline the action plan, findings are categorized by relevant functions such as business, architecture, development, and operations.
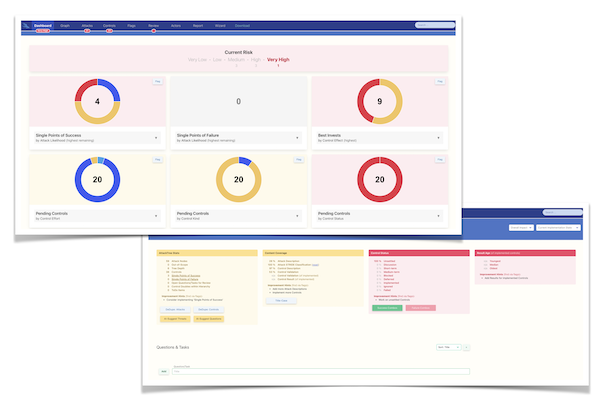
The workshop’s outcome includes various artifacts like diagrams, graphs, and Excel exports, visually representing the current and anticipated reduced risks. As part of my thorough approach, a multistep roadmap for risk mitigation and security enhancement is also provided, guiding your team in implementing these strategies effectively.
Living Threat Models
The use of free tools in all my workshops ensures that you or your team can continually update the threat model and regenerate all report artifacts. This approach transforms the threat model into a dynamic, living entity within your organization, allowing for ongoing refinement and adaptation to new security challenges and architectural changes. This aspect of sustainability and adaptability is crucial in maintaining a current and effective security posture.
Of course, even after the workshop segments conclude, I remain available for any questions or reviews. I am here to provide hints, tips, and guidance on all aspects of threat modeling, ensuring you have the support needed to effectively apply and evolve your threat modeling practices.
Interested in your organization’s individual quote? Let’s talk.