No time for a comprehensive threat modeling workshop — but still want initial results?
Then this quickstart is for you. The Attack Tree Quickstart is a coaching-style engagement that gives you a ready-to-use attack tree with security controls for your product, solution, or architecture — without the overhead of a multi-day workshop.
How it works
The process is lean and async-first:
1. Short intro call (approx. 1 hour)
We kick off with a short scoping call where you walk me through your architecture, solution, or product. I’ll ask targeted questions about key components, trust boundaries, and critical assets.
2. You share available documentation
After the call, you provide whatever architecture information is available — diagrams, design docs, API descriptions, deployment overviews, or even just a whiteboard sketch. No need for perfection; I work with what you have.
3. I create the initial threat model (async)
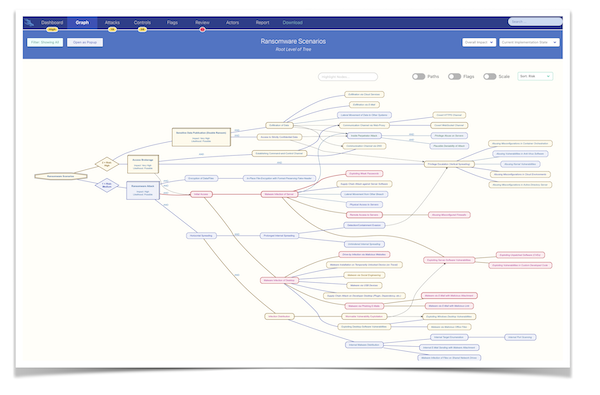
Based on the intro call and your documentation, I build an initial threat model using Attack Tree, covering:
- Attack goals relevant to your specific architecture and business
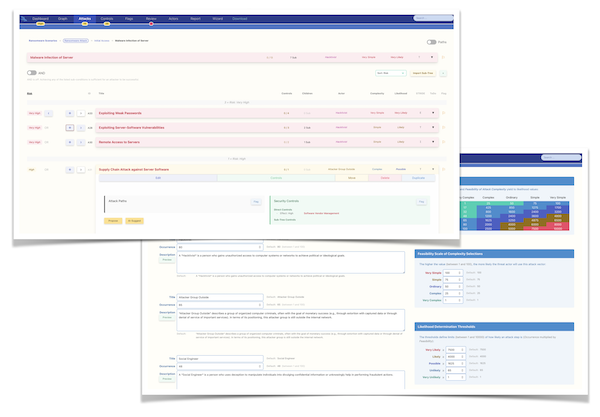
- Attack paths with threat actor assignments and complexity ratings
- Security controls mapped to the identified attack vectors, including implementation status tracking
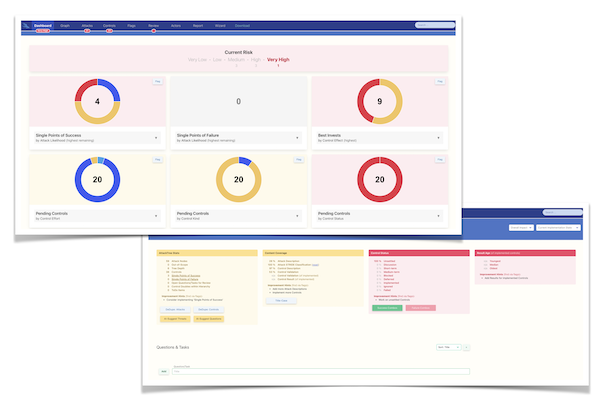
- Risk simulation with initial what-if scenarios
This is where the heavy lifting happens — on my side, not yours.
4. Review call (approx. 1 hour)
We meet again to walk through the draft attack tree together. I explain the identified attack paths and proposed security controls, you add context I might have missed, and we refine the model on the spot. This collaborative review ensures the result matches your reality.
5. The result is yours
After the review call, the finalized attack tree is yours. Since it’s built with the free Attack Tree platform, you can keep evolving it: add new attack paths as your architecture changes, update control statuses as mitigations land, and re-run simulations anytime. You can also regenerate reports and executive summaries on demand as you continue to refine your model.
What you get
- A complete initial attack tree with attack goals, paths, actors, and complexity ratings
- Security controls mapped to attack vectors with effectiveness and cost indicators
- Risk simulation results including prioritized roadmap suggestions
- Full ownership of the model in the free Attack Tree platform, no lock-in, no ongoing costs
- A starting point to continue threat modeling on your own, or to decide if a deeper Agile Threat Modeling workshop makes sense
When does this make sense?
This quickstart is ideal when:
- You need initial threat modeling results fast but can’t allocate multiple days for a full workshop
- You want to evaluate the attack tree approach before committing to a larger engagement
- You’re preparing for a security review or audit and need a structured risk overview quickly
- Your team is new to threat modeling and wants a professionally created starting point to learn from
- You want a second opinion on your architecture’s attack surface from a security and development perspective
Relation to other offerings
The Attack Tree Quickstart is intentionally lightweight. If the initial results reveal a need for deeper analysis, you can transition into a full Agile Threat Modeling workshop or combine the attack tree with a Security Architecture coaching engagement.
For a hands-on validation of the identified attack paths, consider combining this quickstart with an Application Pentest — ask about bundle pricing when both are booked together.
Interested in your individual quote? Let’s talk