Threat modeling agentic AI: a scenario-driven approach
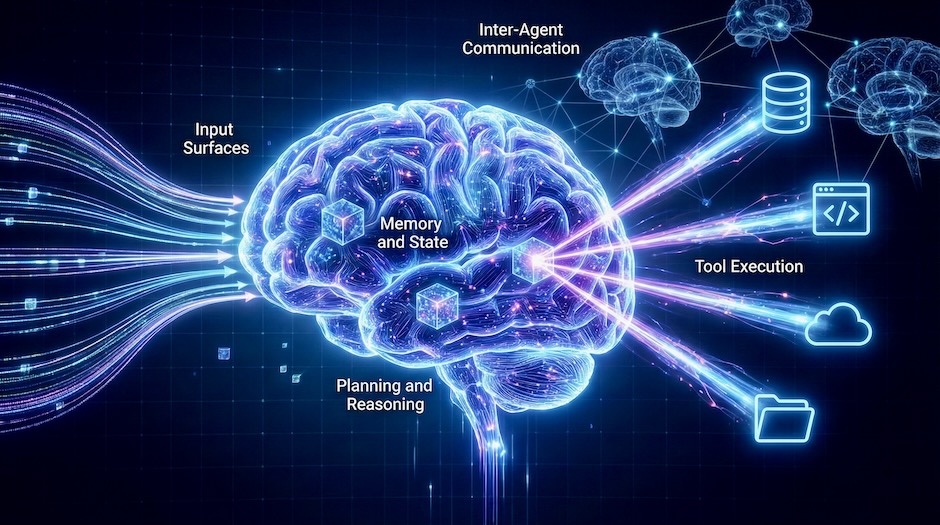
A scenario-driven workflow for tracing attack paths in agentic AI systems using a five-zone navigation lens, attack trees, and OWASP’s threat taxonomy and playbooks.

A scenario-driven workflow for tracing attack paths in agentic AI systems using a five-zone navigation lens, attack trees, and OWASP’s threat taxonomy and playbooks.

I was interviewed about improving cyber resilience through Micro Attack Simulations.